So my first post is about how to set up the environment for Ethernet packet sniffing for external devices.
This allows me to monitor what the device is sending or receiving against the server on the internet. To fetch the packets between the devices with no Wireshark, I need a Ethernet switch with a special function called port mirroring.
The one that I picked is GS308e of NETGEAR which costs about $50.

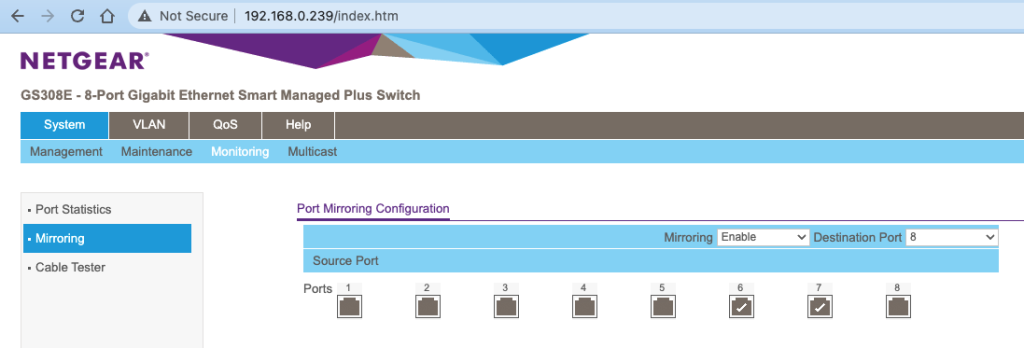
The switch has its own IP address and the web server for configurations and monitoring. Below is how you set up the port mirroring.
With the above set up, all the outgoing packets on port 6 and 7 will be copied to port 8, thus allowing the host on port 8 to monitor the transactions between the devices on port 6 and 7.
I tested the port mirroring using my phone connected to a WiFi router which is then connected to NETGEAR on port 6. On port 7, I have another router connected to the internet.
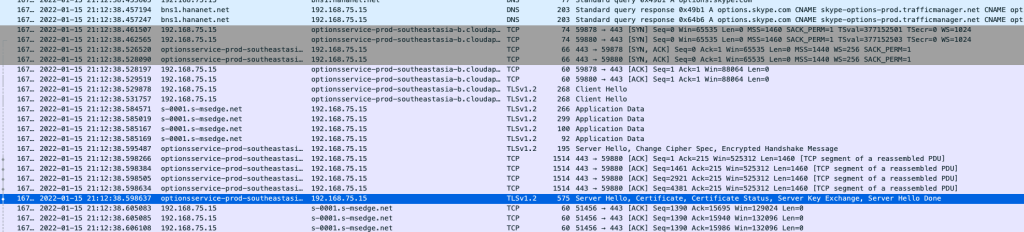
This is a part of Wireshark log on my mac connected on port 8.
These days, most of the transactions are over TLS (SSL), thus packet payloads are all encrypted so it’s not that fun. At least I can see which servers are connected on which time and how much data are transferred.